In today’s increasingly interconnected world, the need for secure and private online experiences has become paramount. Virtual Private Networks (VPNs) play a crucial role in achieving this, offering a secure tunnel for data transmission and masking IP addresses to protect user identities. Understanding the fundamentals of VPN devices and their functionalities is essential for anyone seeking to enhance their online security posture.
Exploring the Basics of VPN Devices

A VPN device, at its core, creates an encrypted connection between your device and a remote server managed by the VPN provider. This encrypted tunnel ensures that all data transmitted between your device and the VPN server is protected from eavesdropping and interception. When you connect to a VPN server, your internet traffic is routed through that server, effectively masking your true IP address and making it appear as if you are browsing from the VPN server’s location.
This process offers several significant benefits. First and foremost, it enhances your online privacy by preventing websites and third-party trackers from identifying your actual location and collecting personal data. Second, it improves your security by encrypting your data, making it virtually unreadable to hackers and cybercriminals who may attempt to intercept your online communications. This is particularly important when using public Wi-Fi networks, which are often unsecured and vulnerable to attacks. Third, it allows you to bypass geographical restrictions and access content that may be blocked in your region. This can be useful for accessing streaming services, social media platforms, or news websites that are unavailable in your current location.
The implementation of a VPN often involves specialized hardware or software. Businesses often deploy dedicated VPN devices, such as routers or firewalls with built-in VPN capabilities, to protect their internal networks and enable secure remote access for employees. Individuals typically use VPN software applications on their computers, smartphones, and tablets to secure their internet connections while browsing the web, streaming content, or engaging in online activities.
The choice of a VPN provider is a critical decision. It is crucial to select a reputable provider with a strong track record of security and privacy. Look for providers that offer robust encryption protocols, a strict no-logs policy, and a wide range of server locations. Furthermore, consider factors such as speed, reliability, and customer support when making your selection.
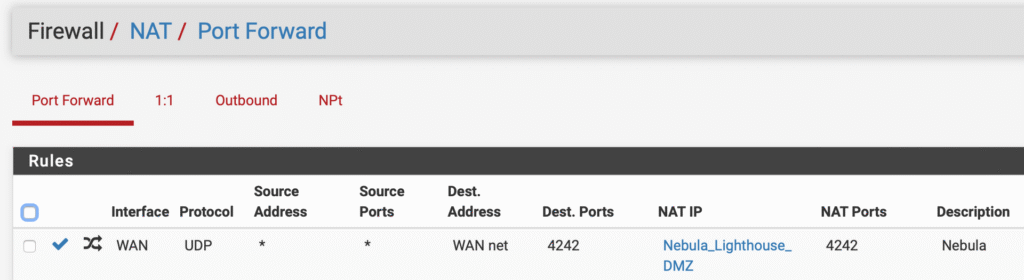
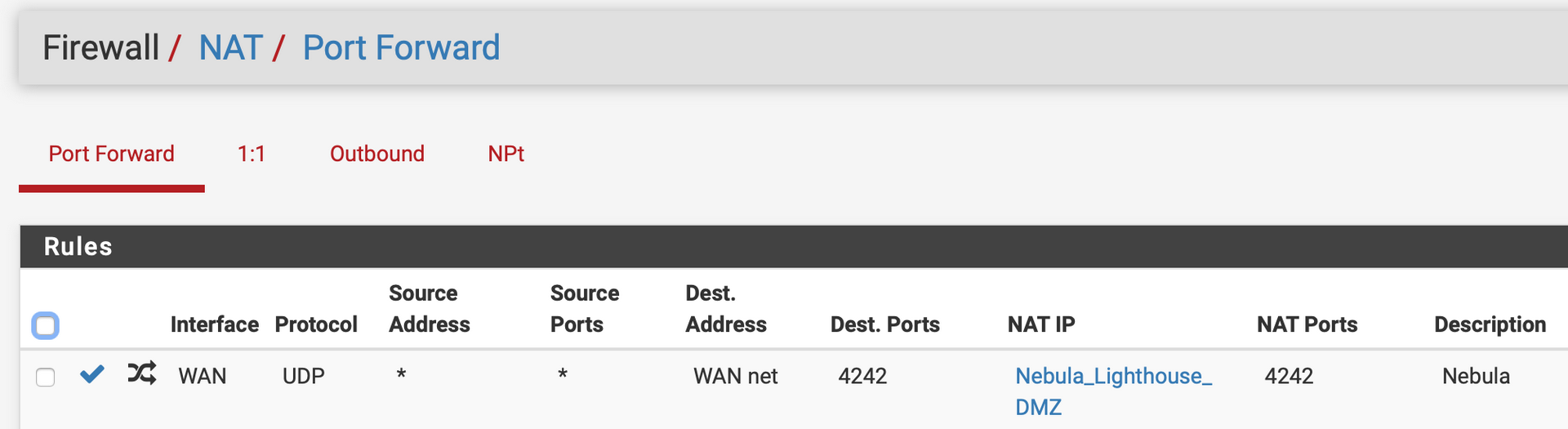
GitHub – shi-hao/mini_vpn: openvpn = ssl/tls + router, this is a router
The concept of a “mini_vpn,” as illustrated by the GitHub project, encapsulates the core functionality of a VPN in a simplified and potentially customizable form. The equation “openvpn = ssl/tls + router” highlights the fundamental components involved: the secure communication protocols (SSL/TLS) combined with the routing capabilities of a router.
This perspective is valuable because it breaks down the complexity of a VPN into its constituent parts. SSL/TLS protocols provide the encryption and authentication necessary to establish a secure connection, while the routing mechanism ensures that data is directed through the VPN server. A project like “mini_vpn” suggests an effort to create a lightweight and potentially more transparent implementation of these principles, allowing users to gain a deeper understanding of how VPNs operate internally.
The implications of such a project are significant. By providing a simplified and accessible VPN implementation, developers and security enthusiasts can experiment with different configurations, analyze the security vulnerabilities, and potentially tailor the VPN to specific needs. This can lead to the development of more secure and efficient VPN solutions, as well as a greater awareness of the underlying technologies.
Furthermore, a “mini_vpn” approach can be particularly useful in resource-constrained environments, such as embedded systems or IoT devices. By optimizing the VPN implementation for these platforms, it becomes possible to secure communication channels in situations where traditional VPN solutions may be too resource-intensive. This opens up new possibilities for secure remote access and data transmission in a wide range of applications.
If you are looking for Exploring the Basics of VPN Devices: What They Are and How They Work you’ve came to the right page. We have 10 Pics about Exploring the Basics of VPN Devices: What They Are and How They Work like GitHub – shi-hao/mini_vpn: openvpn = ssl/tls + router, this is a router, Exploring the Basics of VPN Devices: What They Are and How They Work and also Exploring the Basics of VPN Devices: What They Are and How They Work. Here it is:
Exploring The Basics Of VPN Devices: What They Are And How They Work

locall.host
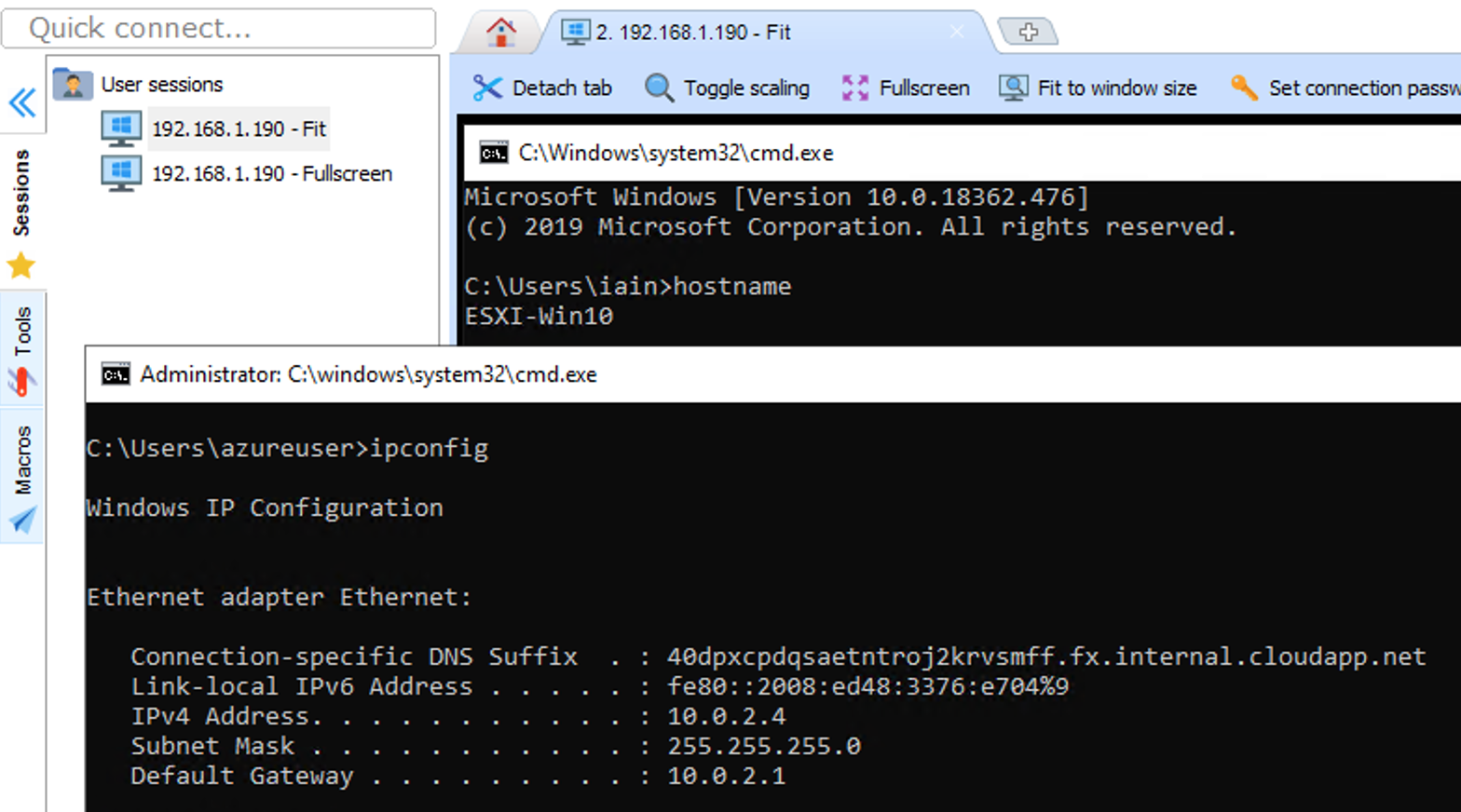
Mini VPN For All!
www.rootisgod.com
vpn mini pros cons
This Blockchain VPN Device Gives You Unlimited Storage

thegadgetflow.com
vpn blockchain device information secures
Portable Hardware VPN Device Färist Micro – Hacker 10 – Security Hacker

hacker10.com
DPN Device Deal: Save 40% And Avoid Recurring Fees | Mashable

mashable.com
GitHub – Shi-hao/mini_vpn: Openvpn = Ssl/tls + Router, This Is A Router
github.com
The Ultimate Guide To Setting Up A VPN Hardware Device
www.vpnunlimited.com
New Mac Mini As VPN Server | MacRumors Forums
forums.macrumors.com
10 Devices You Can Use With A VPN

www.makeuseof.com
Mini VPN For All!
www.rootisgod.com
vpn mini node windows
Mini vpn for all!. Vpn mini node windows. Dpn device deal: save 40% and avoid recurring fees




:max_bytes(150000):strip_icc()/008_how-to-factory-reset-a-lenovo-laptop-5115817-a67348722ce94f9783881ea29e596310.jpg)